 |
| May 26, 2015 | Volume 11 Issue 20 |
Electrical/Electronic News & Products
Designfax weekly eMagazine
Archives
Partners
Manufacturing Center
Product Spotlight
Modern Applications News
Metalworking Ideas For
Today's Job Shops
Tooling and Production
Strategies for large
metalworking plants
Test equipment advancing to meet rapidly changing market needs
 Although the rise of the IoT, 5G, and advanced automotive electronics markets is instigating rapid changes in technology, test equipment is keeping pace, and not just in extensions to bandwidth specifications or signal resolution. Maureen Lipps, Multicomp Pro Private Label Product Segment Leader, Test and Tools, Newark Electronics, runs through important advances in the industry and its tools.
Although the rise of the IoT, 5G, and advanced automotive electronics markets is instigating rapid changes in technology, test equipment is keeping pace, and not just in extensions to bandwidth specifications or signal resolution. Maureen Lipps, Multicomp Pro Private Label Product Segment Leader, Test and Tools, Newark Electronics, runs through important advances in the industry and its tools.
Read the full article.
Smallest rugged AI supercomputer for avionics
 Aitech Systems has released the A178-AV, the latest iteration of its smallest rugged GPGPU AI super-computers available with the powerful NVIDIA Jetson AGX Xavier System-on-Module. With its compact size, the A178-AV is the most advanced solution for artificial intelligence (AI), deep learning, and video and signal processing for next-gen avionic platforms.
Aitech Systems has released the A178-AV, the latest iteration of its smallest rugged GPGPU AI super-computers available with the powerful NVIDIA Jetson AGX Xavier System-on-Module. With its compact size, the A178-AV is the most advanced solution for artificial intelligence (AI), deep learning, and video and signal processing for next-gen avionic platforms.
Learn more.
Touchless angle sensors get CAN SAE J1939 interface
 Novotechnik has added the CAN J1939 interface (developed for heavy-duty vehicles) to its RFC4800 Series of touchless angle sensors measuring angular position up to 360°, turn direction, turns, speed, and operational status. It can provide one or two output channels. It has a longer life and robustness than an optical encoder. It can signal if a sensor needs replacing or average a programmable number of values to output to reduce external noise if present. This is wear-free angle measurement made easy.
Novotechnik has added the CAN J1939 interface (developed for heavy-duty vehicles) to its RFC4800 Series of touchless angle sensors measuring angular position up to 360°, turn direction, turns, speed, and operational status. It can provide one or two output channels. It has a longer life and robustness than an optical encoder. It can signal if a sensor needs replacing or average a programmable number of values to output to reduce external noise if present. This is wear-free angle measurement made easy.
Learn more.
Radar level sensor monitors liquids and powders
 The innovative FR Series non-contact radar level sensor from Keyence has been designed to monitor the level of both liquid and powder in any environment. This sensor features short- and long-range models, as well as chemical and sanitary options to address a wide array of level sensing applications. Works even when obstructions or harsh conditions are present, such as build-up, steam, or turbulence.
The innovative FR Series non-contact radar level sensor from Keyence has been designed to monitor the level of both liquid and powder in any environment. This sensor features short- and long-range models, as well as chemical and sanitary options to address a wide array of level sensing applications. Works even when obstructions or harsh conditions are present, such as build-up, steam, or turbulence.
Learn more.
Raspberry Pi launches $70 AI Kit
 Artificial intelligence (AI) is all the rage, and the makers of Raspberry Pi have created a way for enthusiasts of the single-board computer systems to take part and do a lot of experimenting along the way.
Artificial intelligence (AI) is all the rage, and the makers of Raspberry Pi have created a way for enthusiasts of the single-board computer systems to take part and do a lot of experimenting along the way.
Read the full article.
3D model sharing at Brother Industries cuts rework
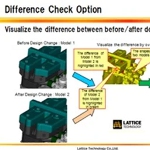 When Brother Industries, maker of printers, computers, and computer-related electronics, deployed Lattice Technology's XVL Player as a viewer for sharing 3D models throughout the processes of product design, parts design, mold design, mold production, and QA of molded parts, they reduced rework significantly -- especially from downstream departments. XVL Studio with its Difference Check Option helped address the rework in mold design, for example, by always keeping everyone informed of design changes.
When Brother Industries, maker of printers, computers, and computer-related electronics, deployed Lattice Technology's XVL Player as a viewer for sharing 3D models throughout the processes of product design, parts design, mold design, mold production, and QA of molded parts, they reduced rework significantly -- especially from downstream departments. XVL Studio with its Difference Check Option helped address the rework in mold design, for example, by always keeping everyone informed of design changes.
Read this real-world case study.
What is 3D-MID? Molded parts with integrated electronics from HARTING
 3D-MID (three-dimensional mechatronic integrated devices) technology combines electronic and mechanical functionalities into a single, 3D component. It replaces the traditional printed circuit board and opens up many new opportunities. It takes injection-molded parts and uses laser-direct structuring to etch areas of conductor structures, which are filled with a copper plating process to create very precise electronic circuits. HARTING, the technology's developer, says it's "Like a PCB, but 3D." Tons of possibilities.
3D-MID (three-dimensional mechatronic integrated devices) technology combines electronic and mechanical functionalities into a single, 3D component. It replaces the traditional printed circuit board and opens up many new opportunities. It takes injection-molded parts and uses laser-direct structuring to etch areas of conductor structures, which are filled with a copper plating process to create very precise electronic circuits. HARTING, the technology's developer, says it's "Like a PCB, but 3D." Tons of possibilities.
Learn more (video included on page).
New! Thermoelectric dehumidifiers for enclosures
 Seifert Systems has just introduced its line of compact Soliflex® Series thermoelectric dehumidifiers, with or without condensate pump. These IP 56-rated units are designed to dehumidify enclosures and small control panels, can be used indoors or outdoors, and are maintenance free. When used with a hygrostat, Soliflex dehumidifiers will keep enclosure humidity below a defined level and only operate when needed.
Seifert Systems has just introduced its line of compact Soliflex® Series thermoelectric dehumidifiers, with or without condensate pump. These IP 56-rated units are designed to dehumidify enclosures and small control panels, can be used indoors or outdoors, and are maintenance free. When used with a hygrostat, Soliflex dehumidifiers will keep enclosure humidity below a defined level and only operate when needed.
Learn more.
More Stego enclosure heater options from AutomationDirect
 Automation-Direct has added more Stego enclosure heaters to their Enclosure Thermal Management lineup. These new 120 to 240 VAC/VDC units include small, flat versions that distribute heat evenly within compact enclosures and are available with 8- or 10-W heating capacities. Also added are compact loop heaters that feature a patented loop body design for increased natural convection airflow, reduced thermal stress on the heater, and better heat transfer. Loop heaters are available in 10- to 150-W heating capacities.
Automation-Direct has added more Stego enclosure heaters to their Enclosure Thermal Management lineup. These new 120 to 240 VAC/VDC units include small, flat versions that distribute heat evenly within compact enclosures and are available with 8- or 10-W heating capacities. Also added are compact loop heaters that feature a patented loop body design for increased natural convection airflow, reduced thermal stress on the heater, and better heat transfer. Loop heaters are available in 10- to 150-W heating capacities.
Learn more.
Great design: Handle with integrated lighting/signaling
 Signaling and indicator lights, switches, and buttons -- elements that hardly any machine can do without. The new JW Winco cabinet U-handle EN 6284 integrates all these functions into a single, compact element. The new U-handle is designed to enhance the operation of systems and machines. It features an integrated button and a large, colored, backlit area on the back of the handle. These elements can be used individually or in combination, providing a versatile tool for system control and process monitoring that can be seen from across the room.
Signaling and indicator lights, switches, and buttons -- elements that hardly any machine can do without. The new JW Winco cabinet U-handle EN 6284 integrates all these functions into a single, compact element. The new U-handle is designed to enhance the operation of systems and machines. It features an integrated button and a large, colored, backlit area on the back of the handle. These elements can be used individually or in combination, providing a versatile tool for system control and process monitoring that can be seen from across the room.
Learn more.
Engineer's Toolbox: What is ground loop feedback?
 Improper grounding can create problems in data logging, data acquisition, and measurement and control systems. One of the most common problems is known as ground loop feedback. Experts at CAS DataLoggers run through five ways to eliminate this problem.
Improper grounding can create problems in data logging, data acquisition, and measurement and control systems. One of the most common problems is known as ground loop feedback. Experts at CAS DataLoggers run through five ways to eliminate this problem.
Read the full article.
AI development kit for multi-camera products
 The QCS6490 Vision-AI Development Kit from Avnet enables engineering teams to rapidly prototype hardware, application software, and AI enablement for multi-camera, high-performance, Edge AI-enabled custom embedded products. The kit facilitates design with the new, energy-efficient MSC SM2S-QCS6490 SMARC compute module based on the Qualcomm QCS6490 processor. Provides support for up to four MIPI CSI cameras and concurrent Mini DisplayPort and MIPI DSI displays.
The QCS6490 Vision-AI Development Kit from Avnet enables engineering teams to rapidly prototype hardware, application software, and AI enablement for multi-camera, high-performance, Edge AI-enabled custom embedded products. The kit facilitates design with the new, energy-efficient MSC SM2S-QCS6490 SMARC compute module based on the Qualcomm QCS6490 processor. Provides support for up to four MIPI CSI cameras and concurrent Mini DisplayPort and MIPI DSI displays.
Learn more.
High-temp cabinet cooler keeps incineration process in business
 An EXAIR client company handles waste treatment on a large ship by operating an incinerator. The area where the incinerator is located gets very hot (over 120° F). This causes failures in the electronics package used to control the incineration process. Since compressed air is readily available, EXAIR's Model HT4225 Cabinet Cooler System is being used to keep the panel cool. It saved the customer from having to replace their control units due to the hot conditions in the incinerator room. Thermostat control is also available, conserving air and operating only when needed to minimize air consumption.
An EXAIR client company handles waste treatment on a large ship by operating an incinerator. The area where the incinerator is located gets very hot (over 120° F). This causes failures in the electronics package used to control the incineration process. Since compressed air is readily available, EXAIR's Model HT4225 Cabinet Cooler System is being used to keep the panel cool. It saved the customer from having to replace their control units due to the hot conditions in the incinerator room. Thermostat control is also available, conserving air and operating only when needed to minimize air consumption.
Learn about EXAIR's huge selection of Cabinet Coolers.
Compact snap-in capacitors for general-purpose applications
 TDK's new EPCOS B43659 series of snap-in aluminum electrolytic capacitors is the next generation of ultra-compact, general-purpose components for voltages of 450 V (DC) featuring an extremely high CV product. It provides the same features and serves the same applications as the previous series but is much more compact. These RoHS-compliant capacitors can be used in a wide range of applications, such as switched-mode power supplies, frequency converters, UPS, medical equipment, and solar inverters.
TDK's new EPCOS B43659 series of snap-in aluminum electrolytic capacitors is the next generation of ultra-compact, general-purpose components for voltages of 450 V (DC) featuring an extremely high CV product. It provides the same features and serves the same applications as the previous series but is much more compact. These RoHS-compliant capacitors can be used in a wide range of applications, such as switched-mode power supplies, frequency converters, UPS, medical equipment, and solar inverters.
Get all the specs.
Conductive Brush Ring overcomes current leakage in EV powertrains
 SKF's new Conductive Brush Ring paves the way to greater reliability and longer life in high-performance electric vehicle powertrain systems. Using pure carbon fiber bristles, it provides a reliable electrical connection between an EV eAxle rotor shaft and its housing. When used in combination with SKF Hybrid ceramic ball bearings, it helps to alleviate parasitic current effects that can lead to premature failure in bearings and other components. Available in different configurations for wet (oil-lubricated) motor designs -- and soon for dry (sealed) applications.
SKF's new Conductive Brush Ring paves the way to greater reliability and longer life in high-performance electric vehicle powertrain systems. Using pure carbon fiber bristles, it provides a reliable electrical connection between an EV eAxle rotor shaft and its housing. When used in combination with SKF Hybrid ceramic ball bearings, it helps to alleviate parasitic current effects that can lead to premature failure in bearings and other components. Available in different configurations for wet (oil-lubricated) motor designs -- and soon for dry (sealed) applications.
Learn more.
College researchers hack teleoperated surgical robot to reveal security flaws
By Jennifer Langston, University of Washington
To make cars as safe as possible, we crash them into walls to pinpoint weaknesses and better protect people who use them.
That's the idea behind a series of experiments conducted by a University of Washington engineering team that hacked a next-generation teleoperated surgical robot -- one used only for research purposes -- to test how easily a malicious attack could hijack remotely controlled operations in the future and to make those systems more secure.
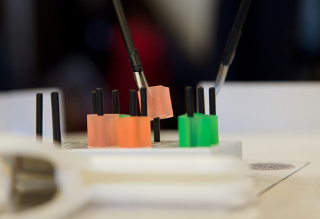
UW researchers mounted cyberattacks while study participants used a teleoperated surgical robotic system to move blocks on a pegboard. [University of Washington]
Real-world teleoperated robots, which are controlled by a human who may be in another physical location, are expected to become more commonplace as the technology evolves. They're ideal for situations that are dangerous for people: fighting fires in chemical plants, diffusing explosive devices, or extricating earthquake victims from collapsed buildings.
Outside of a handful of experimental surgeries conducted remotely, doctors typically use surgical robots today to operate on a patient in the same room using a secure, hard-wired connection. But telerobots may one day routinely provide medical treatment in underdeveloped rural areas, battlefield scenarios, Ebola wards, or catastrophic disasters happening half a world away.
In two recent papers, UW BioRobotics Lab researchers demonstrated that next-generation teleoperated robots using nonprivate networks -- which may be the only option in disasters or in remote locations -- can be easily disrupted or derailed by common forms of cyberattacks. Incorporating security measures to foil those attacks, the authors argue, will be critical to their safe adoption and use.
"We want to make the next generation of telerobots resilient to some of the threats we've detected without putting an operator or patient or any other person in the physical world in danger," said lead author Tamara Bonaci, a UW doctoral candidate in electrical engineering.
To expose vulnerabilities, the UW team mounted common types of cyberattacks as study participants used a teleoperated surgical robot developed at the UW for research purposes to move rubber blocks between pegs on a pegboard.
By mounting "man in the middle" attacks, which alter the commands flowing between the operator and robot, the team was able to maliciously disrupt a wide range of the robot's functions -- making it hard to grasp objects with the robot's arms -- and even to completely override command inputs. During denial-of-service attacks, in which the attacking machine flooded the system with useless data, the robots became jerky and harder to use.
In some cases, the human operators were eventually able to compensate for those disruptions, given the relatively simple task of moving blocks. In situations where precise movements can mean the difference between life and death -- such as surgery or a search-and-rescue extrication -- these types of cyberattacks could have more serious consequences, the researchers believe.
With a single packet of bad data, for instance, the team was able to maliciously trigger the robot's emergency stop mechanism, rendering it useless.
The tests were conducted with the Raven II, an open-source teleoperated robotic system developed by UW electrical engineering professor Blake Hannaford and former UW professor Jacob Rosen, along with their students. Raven II, currently manufactured and sold by Seattle-based Applied Dexterity, a UW spin-out, is a next-generation teleoperated robotic system designed to support research in advanced techniques of robotic-assisted surgery. The system is not currently in clinical use and is not approved by the FDA.
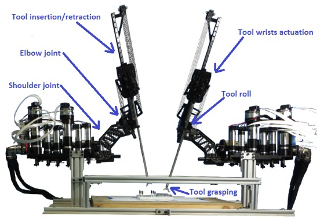
Raven II was developed by UW researchers to explore the boundaries of robotic-assisted surgery. [University of Washington]
The surgical robots that are FDA approved for clinical use today, which typically allow a surgeon to remove tumors, repair heart valves, or perform other procedures in a less-invasive way, use a different communication channel and typically do not rely on publicly available networks, which would make the cyberattacks the UW team tested much harder to mount.
But if teleoperated robots will be used in locations with no secure alternative to networks or other communication channels that are easy to hack, it's important to begin designing and incorporating additional security features now, the researchers argue.
"If there's been a disaster, the network has probably been damaged too. So you might have to fly a drone and put a router on it and send signals up to it," said Howard Chizeck, UW professor of electrical engineering and co-director of the UW BioRobotics Lab.
"In an ideal world, you'd always have a private network and everything could be controlled, but that's not always going to be the case. We need to design for and test additional security measures now, before the next generation of telerobots is deployed."
Encrypting data packets that flow between the robot and human operator would help prevent certain types of cyberattacks. But it isn't effective against denial-of-service attacks that bog down the system with extraneous data. With video, encryption also runs the risk of causing unacceptable delays in delicate operations.
The UW team is also developing the concept of "operator signatures," which leverage the ways in which a particular surgeon or other teleoperator interacts with a robot to create a unique biometric signature.
By tracking the forces and torques that a particular operator applies to the console instruments and his or her interactions with the robot's tools, the researchers have developed a novel way to validate that person's identity and authenticate that the operator is the person he or she claims to be.
Moreover, monitoring those actions and reactions during a telerobotic procedure could give early warning that someone else has hijacked that process.
"Just as everyone signs something a little bit differently and you can identify people from the way they write different letters, different surgeons move the robotic system differently," Chizeck said. "This would allow us to detect and raise the alarm if all of a sudden someone who doesn't seem to be operator A is maliciously controlling or interfering with the procedure."
Co-authors on the three telerobotic security papers include UW electrical engineering graduate students Junjie Yan and Jeffrey Herron, Tadayoshi Kohno of the UW computer science and engineering department, former UW computer science and engineering undergraduate Tariq Yusuf, Ryan Calo of the UW School of Law, and law student Aaron Alva.
The research was funded by the National Science Foundation.
Published May 2015
Rate this article
View our terms of use and privacy policy
